The face of malware has changed over recent years and it’s safe to say that it’s become an industry like any other. Your data, and it’s importance to you, has a value and it’s one that people are only to keen to capitalise on. With ransomware such as CryptoLocker and Locky, this is something that’s become all too easy.
In your organisation you’ll have several tools in your arsenal which can be put to good use – mail filtering, gateway AV, web filtering, but one which you really should be making use of is the File Screening feature of your Windows servers. This allows you to build rulesets to report on, or block, files on your server.
[message type=”info” title=”Update”]If you need a quick way to configure File Server Resource Manager then check out this awesome script I’ve found. [/message]
[message type=”warning” title=”Revisions”]24th May 2016 – ESET have released a decrypter for TeslaCrypt which may help you out.
8th April 2016 – Updated to include Maktub files.
14th April 2016 – Update for Jigsaw ransomware.[/message]
I’m going to look at how to block many of the filetypes associated with CryptoLocker and Locky.
- First thing to do is to install the File Server Resource Manager Role on your Windows server, either 2008, 2008 R2, 2012 or 2012 R2. Do this from the Manage > Add Roles and Features menu in Server Manager.
[space height=”20″]
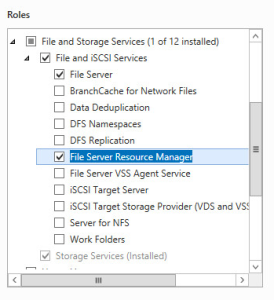
- You can now load the File Server Resource Manager from Administrative Tools.
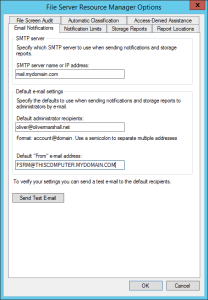
- Right click the File Server Resource Manager top level node on the left hand nav bar and choose Configure Options. This is where you’ll configure your email settings. Enter your email server information and hit the Test button to ensure you get a test email back, then click OK.
[space height=”20″]
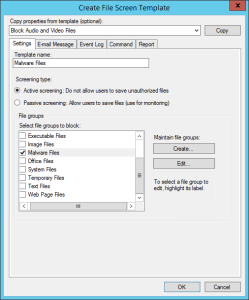
- Right click the File Groups nav node and choose Create File Group. Create a new group called Malware Files and add the files you want to exclude. In this case I’m using the following list which I’ll update as I find new file names. If you don’t want to paste all these in then you can use the handy powershell command at the bottom of this post to create the File Group and then skip this step.
[space height=”20″]_Locky_recover_instructions.txt DECRYPT_INSTRUCTIONS.TXT DECRYPT_INSTRUCTIONS.HTML DECRYPT_INSTRUCTION.TXT DECRYPT_INSTRUCTION.HTML HELP_DECRYPT.TXT HELP_DECRYPT.HTML DecryptAllFiles.txt enc_files.txt HowDecrypt.txt How_Decrypt.txt How_Decrypt.html HELP_TO_DECRYPT_YOUR_FILES.txt HELP_RESTORE_FILES.txt HELP_TO_SAVE_FILES.txt restore_files*.txt restore_files.txt RECOVERY_KEY.TXT how to decrypt aes files.lnk HELP_DECRYPT.PNG HELP_DECRYPT.lnk DecryptAllFiles*.txt Decrypt.exe ATTENTION!!!.txt AllFilesAreLocked*.bmp MESSAGE.txt _DECRYPT_INFO_* *.locky *.ezz *.ecc *.exx *.7z.encrypted *.ctbl *.encrypted *.aaa *.xtbl *.abc *.JUST *.EnCiPhErEd *.cryptolocker *.micro *.FUN *.KKK *.GWS *.BTC
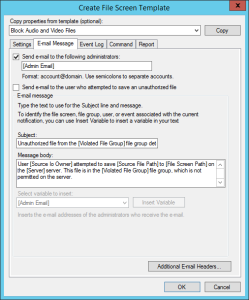
- Next up, right click the File Screen Templates node and choose Create File Screen Template. In my example I’ve called it Malware Files. Select the “Malware Files” group from the list of groups shown then click on the email tab. Here you want to enable email alerts – you really want to be told if you have some ransomware on your server – and click OK.
[space height=”20″]
[one_half]
 [/one_half][one_half_last]
[/one_half][one_half_last]
 [/one_half_last]
[/one_half_last] - Now we want to apply our template to our file locations. Right click the File Screens node and choose Create File Screen. Choose the folder to assign the file screening template to and choose the template that you create before. Click Ok.
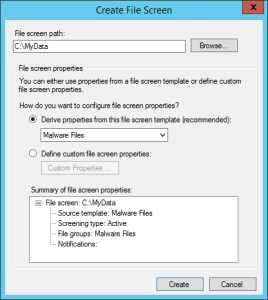
- If you open a command prompt you can test what will happen. Pop in to your folder and try creating a malicious looking file. You should also receive an email if you’ve enabled email alerts.

Powershell
To help with adding the file names that need to be blocked, you can use this powershell command. Just paste it in to the powershell prompt on the server and the File Screen Group will be created for you. You will then just need to create a template and assign it to a folder.
Windows 2012
New-FsrmFileGroup -Name "Malware Files" –IncludePattern @("*.FUN","*.KKK","*.GWS","*.BTC","_DECRYPT_INFO_*","_Locky_recover_instructions.txt","DECRYPT_INSTRUCTIONS.TXT", "DECRYPT_INSTRUCTIONS.HTML", "DECRYPT_INSTRUCTION.TXT", "DECRYPT_INSTRUCTION.HTML", "HELP_DECRYPT.TXT", "HELP_DECRYPT.HTML", "DecryptAllFiles.txt", "enc_files.txt", "HowDecrypt.txt", "How_Decrypt.txt", "How_Decrypt.html", "HELP_TO_DECRYPT_YOUR_FILES.txt", "HELP_RESTORE_FILES.txt", "HELP_TO_SAVE_FILES.txt", "restore_files*.txt", "restore_files.txt", "RECOVERY_KEY.TXT", "how to decrypt aes files.lnk", "HELP_DECRYPT.PNG", "HELP_DECRYPT.lnk", "DecryptAllFiles*.txt", "Decrypt.exe", "ATTENTION!!!.txt", "AllFilesAreLocked*.bmp", "MESSAGE.txt","*.locky","*.ezz", "*.ecc", "*.exx", "*.7z.encrypted", "*.ctbl", "*.encrypted", "*.aaa", "*.xtbl", "*.abc", "*.JUST", "*.EnCiPhErEd", "*.cryptolocker","*.micro")
Windows 2008/R2
filescrn Filegroup Add /Filegroup:"Ransomware Files" /Members:"*.FUN|*.KKK|*.GWS|*.BTC|_DECRYPT_INFO_*|_Locky_recover_instructions.txt|DECRYPT_INSTRUCTIONS.TXT|DECRYPT_INSTRUCTIONS.HTML|DECRYPT_INSTRUCTION.TXT|DECRYPT_INSTRUCTION.HTML|HELP_DECRYPT.TXT|HELP_DECRYPT.HTML|DecryptAllFiles.txt|enc_files.txt|HowDecrypt.txt|How_Decrypt.txt|How_Decrypt.html|HELP_TO_DECRYPT_YOUR_FILES.txt|HELP_RESTORE_FILES.txt|HELP_TO_SAVE_FILES.txt|restore_files*.txt|restore_files.txt|RECOVERY_KEY.TXT|how to decryp t aes files.lnk|HELP_DECRYPT.PNG|HELP_DECRYPT.lnk|DecryptAllFiles*.txt|Decrypt.exe|ATTENTION!!!.txt|AllFilesAreLocked*.bmp|MESSAGE.txt|*.locky|*.ezz|*.ecc|*.exx|*.7z.encrypted|*.ctbl|*.encrypted|*.aaa|*.xtbl|*.abc|*.JUST|*.EnCiPhErEd|*.cryptolocker|*.micro"


 [/one_half][one_half_last]
[/one_half][one_half_last] [/one_half_last]
[/one_half_last]




